Open-source tools to analyze your AWS environment (2/3)
This article is part of a series about
open-sourcetools and AWS, in which I will share those tools that I have tested and that I think you may find useful.1/3: Getting Started with AWS open-source tools: main open-source tools and extend AWS CLI (this article).
2/3: Analyze your AWS environment: focus on the inventory, analysis and security assessment of the AWS environment.
3/3: How to help you with your code: to generate it (IaC), validate it (policy as code and compliance) and analyze it (static analysis/credentials).
1. Introduction
In this article, we will focus on the inventory, analysis and security assessment of the AWS environment.
Some open-source tools could appear in several categories (in this same article or among the 3 open-source tools articles). I thought it was better not to mix information between categories when a tool could be part of several of them.
2. Inventory and analyze your environment
These open-source tools are useful to analyze all of your AWS environment:
- General
- cloudmapper:
Analyzeyour AWS environment - prowler:
Quick analysisof your AWS environment
- cloudmapper:
- IAM (specific)
- AirIAM: Detect
IAM unused resources: users, access keys, roles, groups, policies and policy attachments
- AirIAM: Detect
2.1. cloudmapper
CloudMapper helps you analyze your Amazon Web Services (AWS) environment.
Based on Python components.
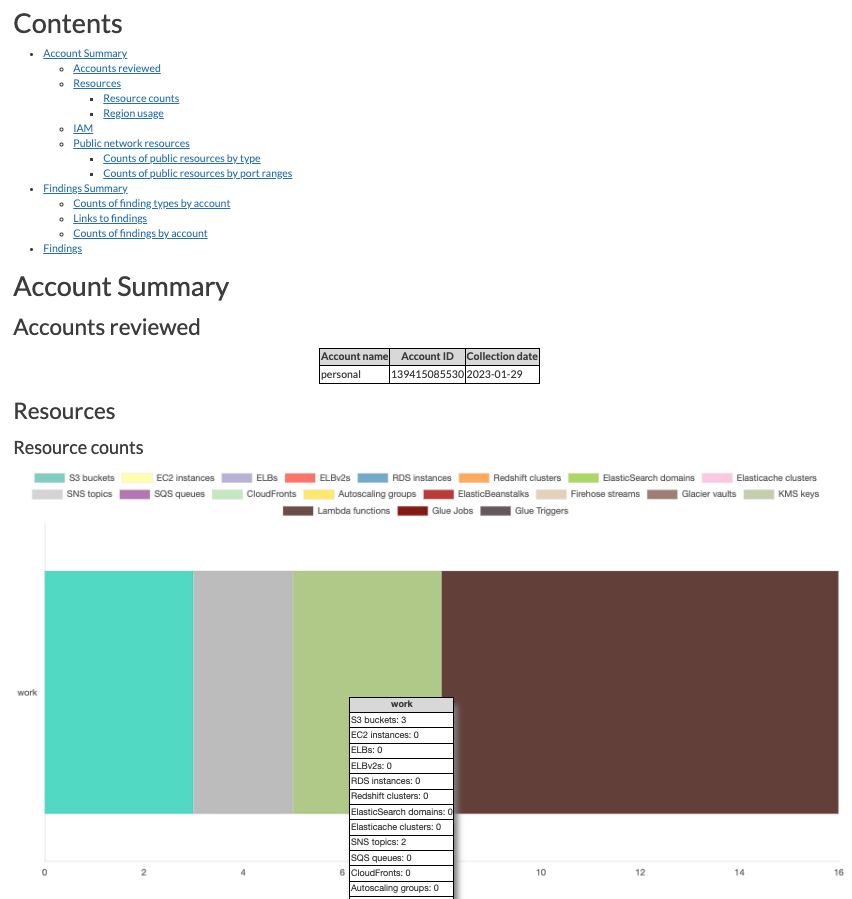
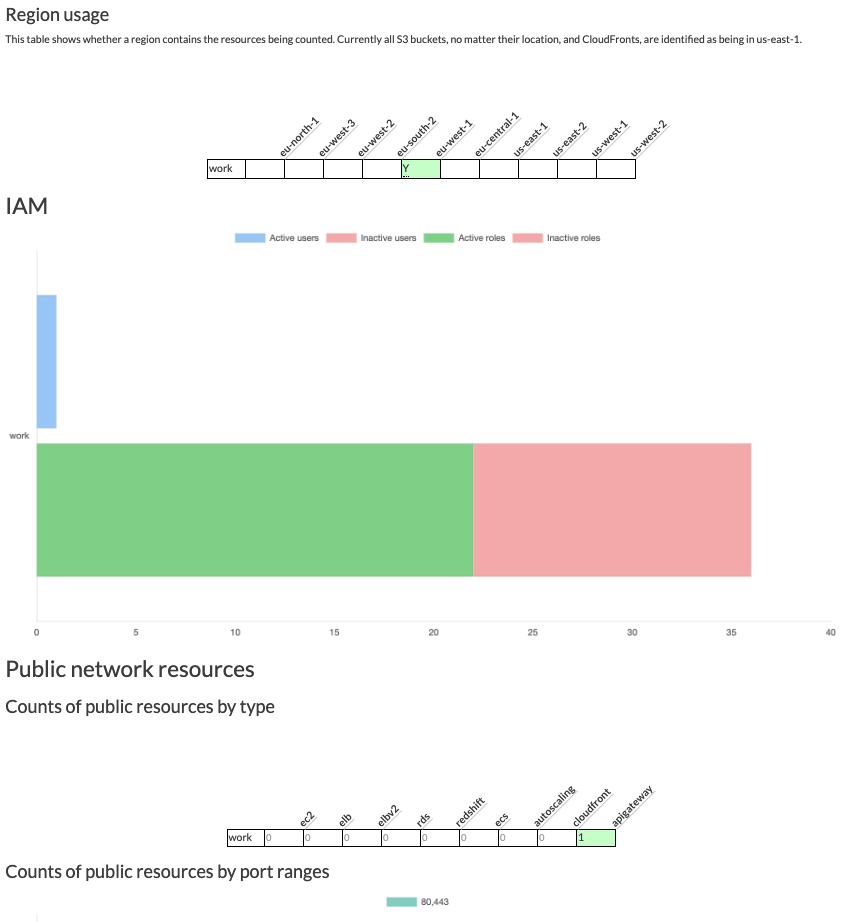
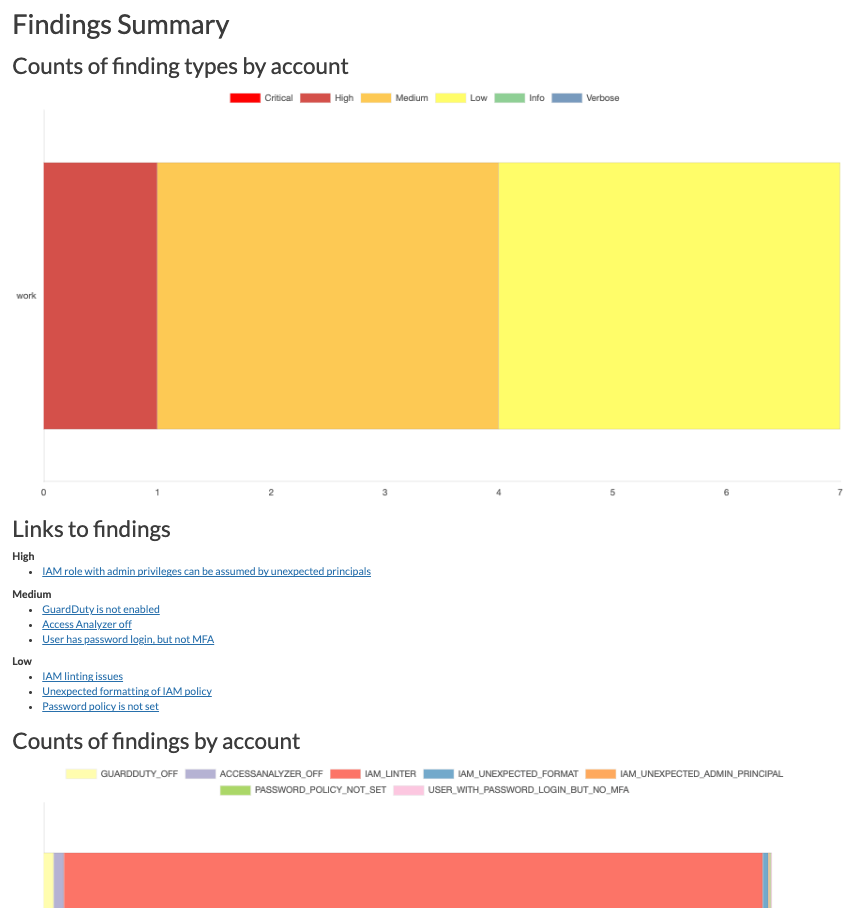
Why use it: Analyze your AWS environment: review status of the account, resource inventory (all resources in all the regions and region usage), IAM resources (active/inactive), public resources (ec2, elb, elbv2, rds, redshift, ecs, autoscaling, cloudfront and apigateway) and finally findings of security (a few).
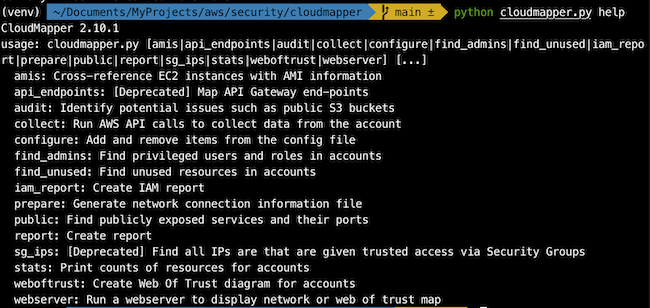
List of the commands of this tool:
The shortcut is:
Run the
collectcommand to get your resources (you can filter the regions that you want using the--regions 'eu-west-1,eu-west-2'… us-east-1 will be always added)Then run the
reportcommand (an html page will be generated with all the information)A specific command that I like is the
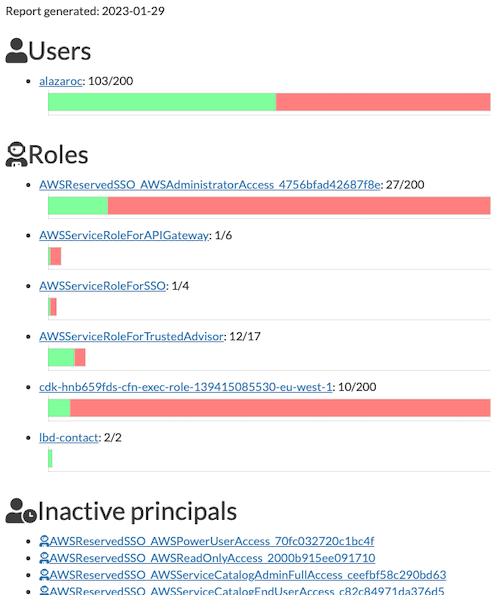
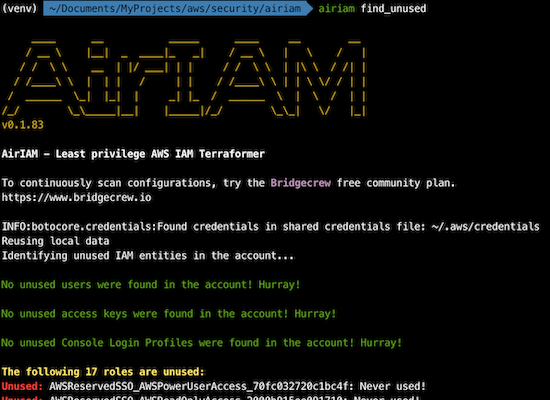
iam_reportbecause it allows you review unused permissions in your IAM resources:
Is it popular?: On GitHub: Watch 135; Fork 759; Stars 5.3K
Recently updated? No. The last commit was on Jul 25, 2022 (956 commits). Additionally, some original functionality of this tool is now deprecated (generation of networking diagrams)
URL: https://github.com/duo-labs/cloudmapper
There is a CDK project to run in Fargate service the CloudMapper’s collection and audit capabilities nightly, across multiple accounts, sending any audit findings to a Slack channel and keeping a copy of the collected metadata in an S3 bucket. This is the diagram of the solution https://github.com/duo-labs/cloudmapper/blob/main/auditor/README.md
2.2. prowler
Prowler is an Open Source security tool… and you will find all this information in the following section (this is for inventory and analysis of the environment).
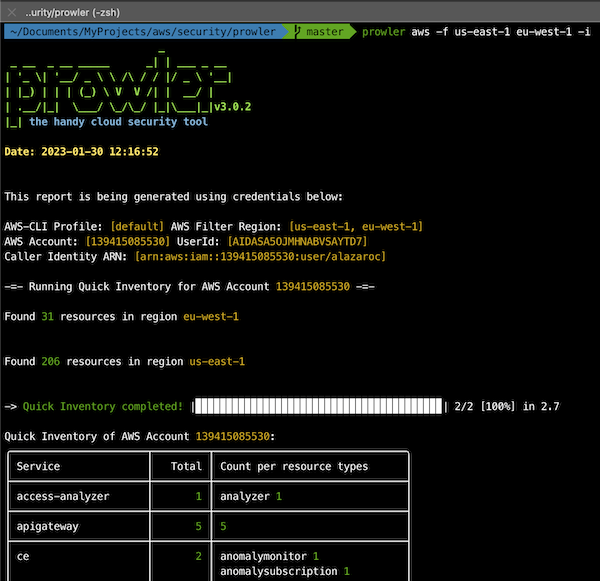
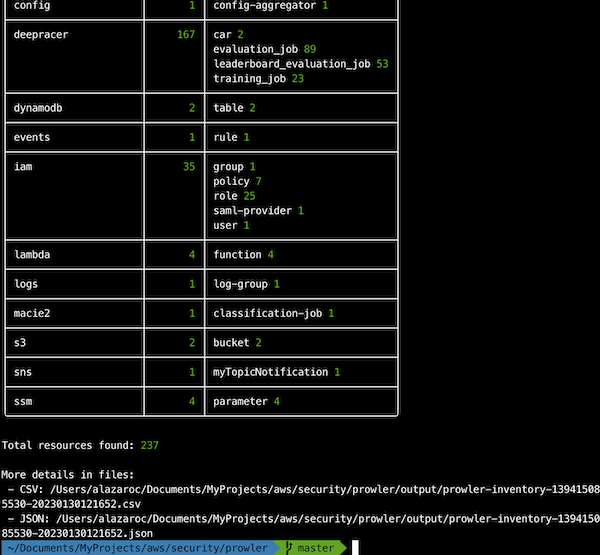
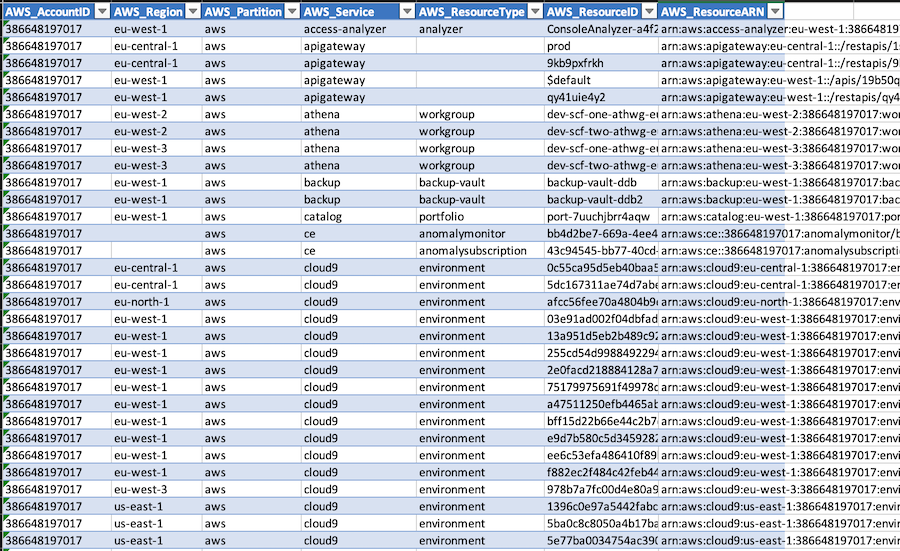
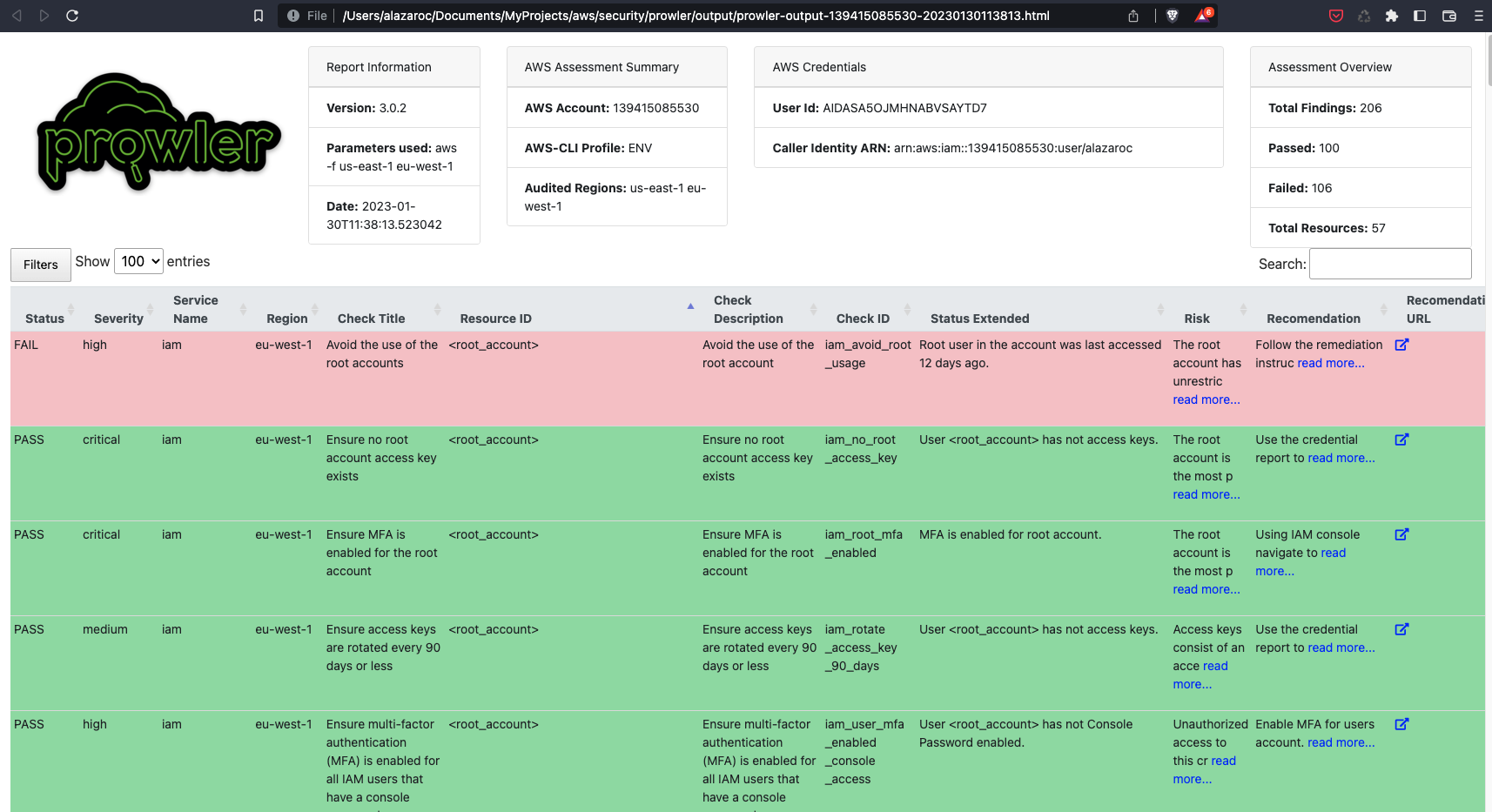
prowler has the functionality to perform a quick inventory check. It will give you in the console information about the number of each resource that you have, and in json/csv generated files you will find information about what is the specific resource (region, aws service, resource type, resource id and ARN)
Why use it: Perform a quick analysis of your AWS environment (a few seconds).
And this is the CSV file report:
Is it popular?: On GitHub: Watch 122; Fork 1.1k; Stars 7.6K
Recently updated? Last commit yesterday (at the time I am writing this post). Total commits 2271
URL: https://github.com/prowler-cloud/prowler
2.3. AirIAM
AirIAM scans existing IAM usage patterns and provides a simple method to migrate IAM configurations into a right-sized Terraform plan. It identifies unused users, roles, groups, policies and policy attachments and replaces them with a Least Privileges Terraform code modelled to manage AWS IAM.
AirIAM was created to promote immutable and version-controlled IAM management to replace today’s manual and error-prone methods.
Why use it: IAM scan tool to detect unused resources (based on Amazon Access Advisor APIs) and the creation of terraform templates of your IAM resources.
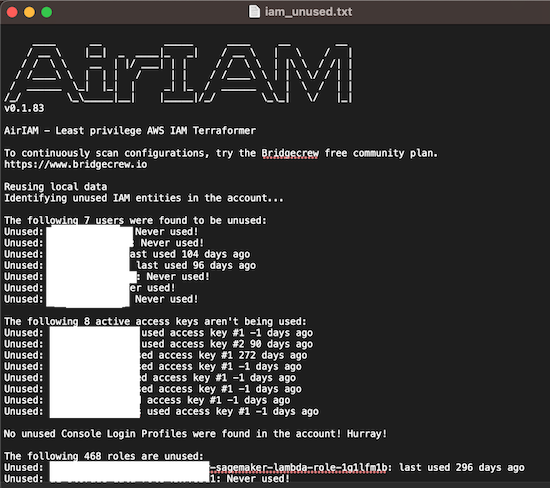
This is another example analyzing other AWS account and exporting the results in a txt file:
Is it popular?: On GitHub: Watch 15; Fork 68; Stars 673
Recently updated? No. Last commit was on Aug 2, 2022. In total, 426 commits.
URL: https://github.com/bridgecrewio/AirIAM
Updated:
The first time I used this tool, the Terraform template generation functionality worked fine, but now I receive an error and was not able to use it. However, I think that this tool is useful to find this iam unused resources
2.4. Summary: Which tool should I use to analyze my environment?
It depends on what you want to do:
- Full analysis of the AWS environment:
cloudmapper - Get a quick inventory of the AWS environment:
prowler - Fast IAM unused resources analysis:
AirIAM - Apply least-privilege to IAM roles (review which permissions you are not using):
cloudmapper
3. Security Assessment
There are many different tools to realize a security assessment of your environment.
- General
- prowler:
security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness - Scoutsuite: multi-cloud
security-auditing tool, which enables security posture assessment of cloud environments - cloudsploit: Cloud Security Scans to detect
potential misconfigurations and security risks - steampipe yes, AGAIN. Ensure that cloud resources comply with security benchmarks such as CIS, NIST, and SOC2.
- prowler:
- IAM
- cloudsplaining:
IAM Security Assessment tool
- cloudsplaining:
3.1. prowler
This is the second time I have mentioned prowler in this article in two different categories.
Prowler is an Open Source security tool to perform AWS and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness.
It contains more than 240 controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks.
There are 4 available categories:
- secrets
- trust-boundaries
- internet-exposed
- forensics-ready
There are 3 available Compliance Frameworks:
- cis_1.4_aws
- cis_1.5_aws
- ens_rd2022_aws
severity:
- informational
- low
- medium
- high
- critical
Why use it: Security tool to perform security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness.
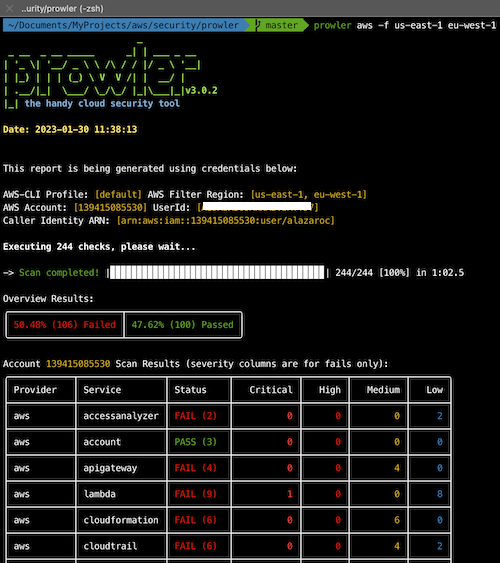
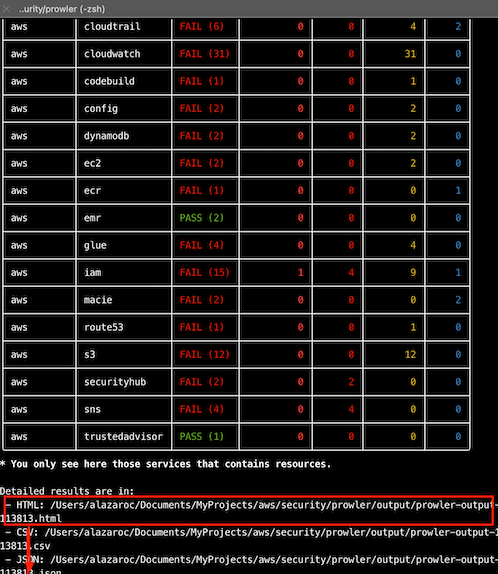
By default, prowler will scan all AWS regions. If you want analyze only a few regions you can use the following command
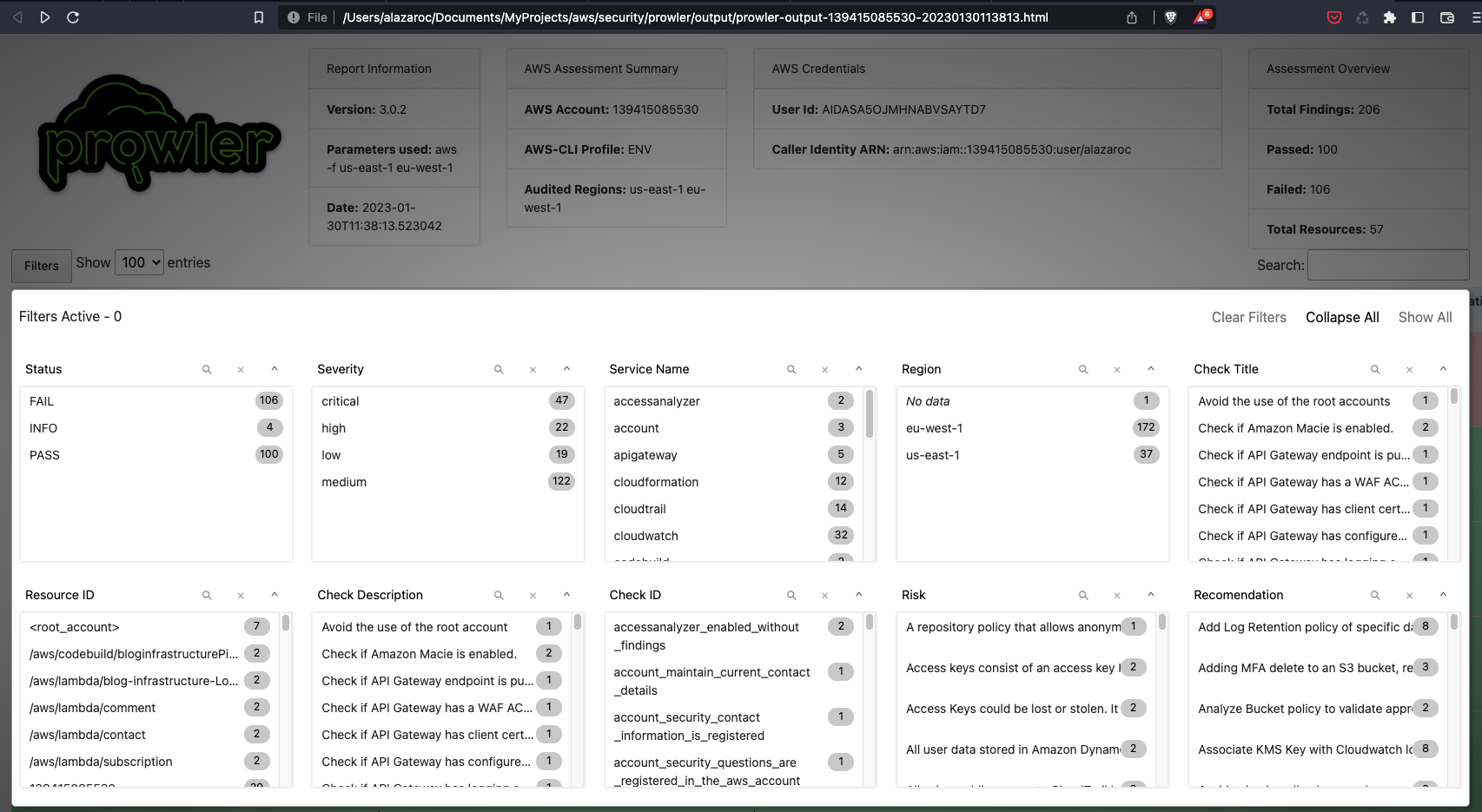
-f us-east-1 eu-west-1 ...And this is the HTML file report:
Is it popular?: On GitHub: Watch 122; Fork 1.1k; Stars 7.6K
Recently updated? Last commit yesterday (at the time I am writing this post). Total commits 2271
URL: https://github.com/prowler-cloud/prowler
3.2. Scoutsuite
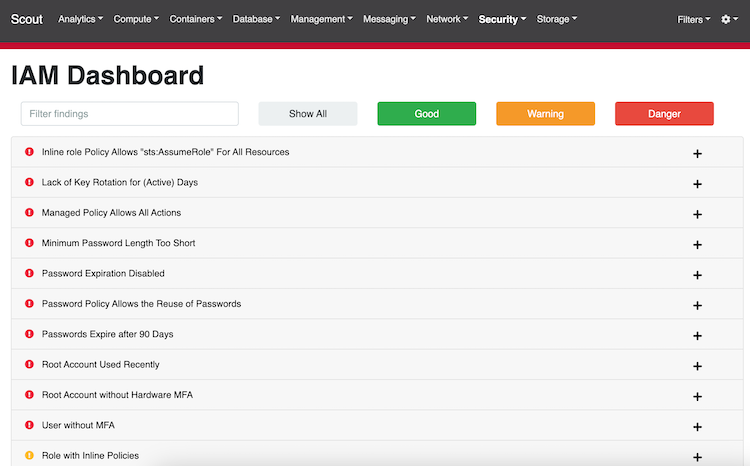
Scout Suite is an open-source multi-cloud security-auditing tool`, which enables security posture assessment of cloud environments. Using the APIs exposed by cloud providers, Scout Suite gathers configuration data for manual inspection and highlights risk areas. Rather than going through dozens of pages on the web consoles, Scout Suite presents a clear view of the attack surface automatically.
Scout Suite was designed by security consultants/auditors. It is meant to provide a point-in-time security-oriented view of the cloud account it was run in. Once the data has been gathered, all usage may be performed offline.
Why use it: Enable security posture assessment of cloud environments.
By default, scoutsuite will scan all AWS regions. If you want analyze only a few regions you can use the following command
-r us-east-1 eu-west-1 ...
Is it popular?: On GitHub: Watch 113; Fork 816; Stars 5K
Recently updated?: No. Last commit was on Sep 5, 2022 (6101 commits in total)
URL: https://github.com/nccgroup/ScoutSuite
I didn’t found information about what security frameworks is using or more information about the security controls. However, the findings in the audit report are useful and you have to review them!
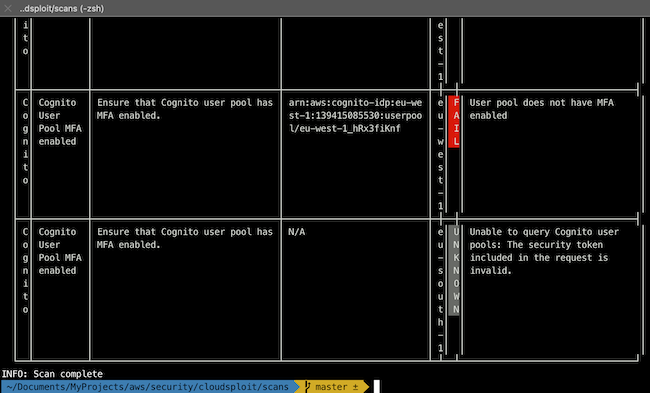
3.3. cloudsploit
CloudSploit by Aqua is an open-source project designed to detect security risks in cloud infrastructure accounts, including Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI), and GitHub. These scripts are designed to return a series of potential misconfigurations and security risks.
Compliance:
- hipaa
- PCI
- CIS (level 1 and 2)
Why use it: detect potential misconfigurations and security risks in your AWS account
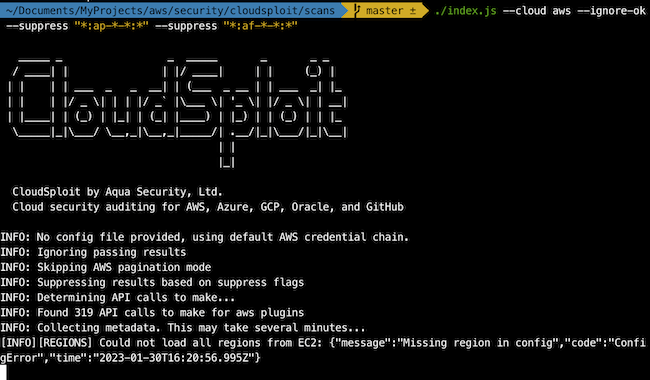
However, in the console the result is not clear:
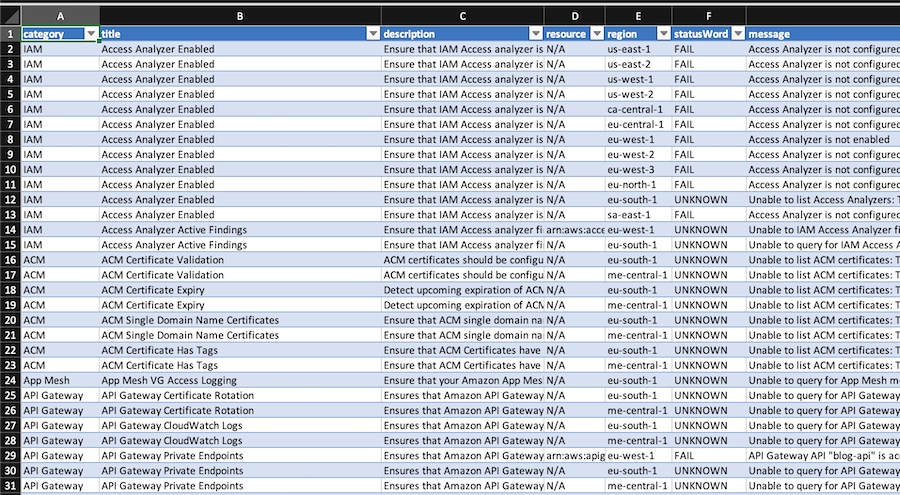
A better solution is generate the report in a csv file adding the following command
--csv=file.csv. After convert the csv into a table it will look like this:
Is it popular?: On GitHub: Watch 70; Fork 575; Stars 2.5k
Recently updated?: Yes. Last commit was 3 weeks ago (3449 commits in total)
URL: https://github.com/aquasecurity/cloudsploit
I didn’t found how to scan only a few regions. In the official documentation only is included how to suppress all one region results
./index.js --suppress *:us-east-1:*. And to exclude more than one region you can use something like this--suppress "*:ap-*-*:*" --suppress "*:af-*-*:*" ...
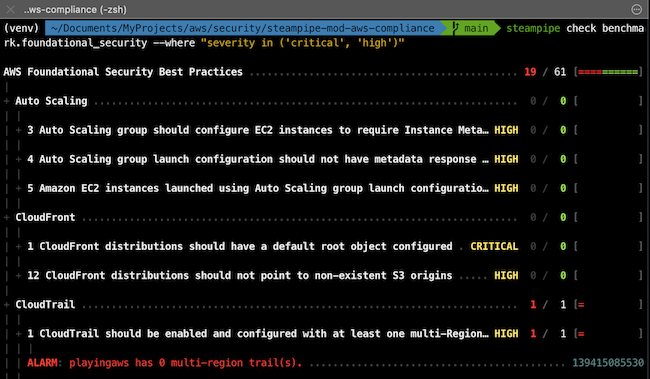
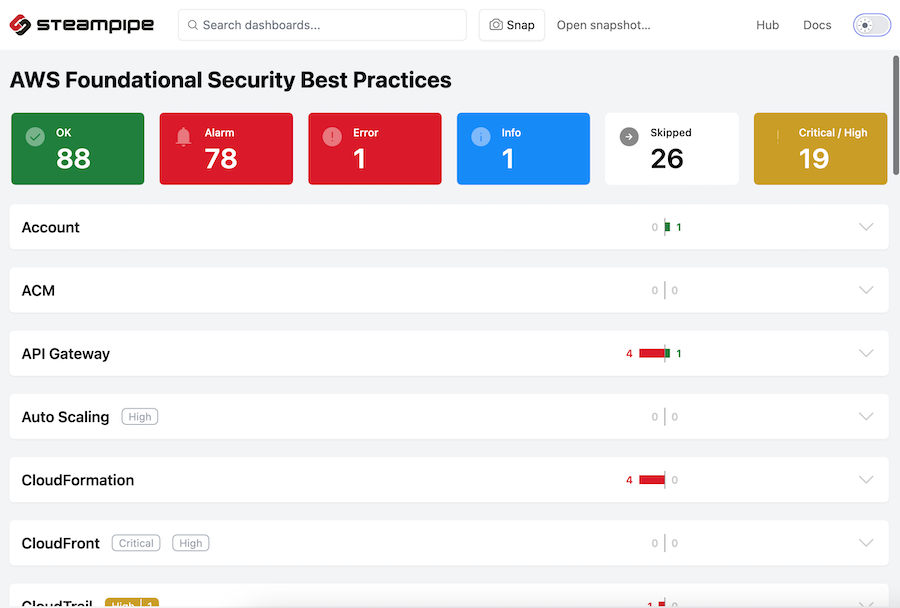
3.4. steampipe
I mentioned this tool in my first article about open-source when I talked about Extend CLI capabilities here
Steampipe is the universal interface to APIs, and you can use SQL to query cloud infrastructure, SaaS, code, logs, and more.
Besides, I am going to show you two new capabilities:
- Check:
Ensure that cloud resources comply with security benchmarkssuch as CIS, NIST, and SOC2.- AWS security best practices contains 180 controls
- CIS v1.50 contains 63 controls
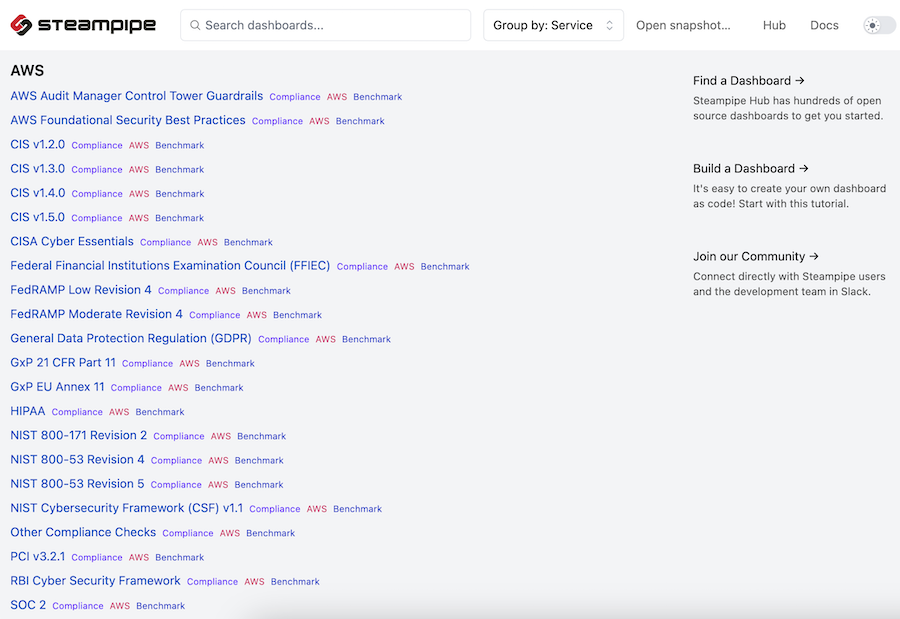
- Visualize: View
prebuilt dashboardsor build your own.
Why use it: for me, the benchmark of AWS security best practices with 180 controls and the CIS level 1.5 with 63 are enough to consider use this tool to perform a security analysis.
Is it popular?: On GitHub: Watch 32; Fork 171; Stars 4.6k
Recently updated? Yes, last commit 2 days ago. Total commits 2007
URL: https://github.com/turbot/steampipe
More information (checks and dashboard):
- https://steampipe.io/docs/check/overview
- https://steampipe.io/docs/dashboard/overview
- https://aws.amazon.com/blogs/opensource/compliance-auditing-with-steampipe-and-sql/
3.5. cloudsplaining
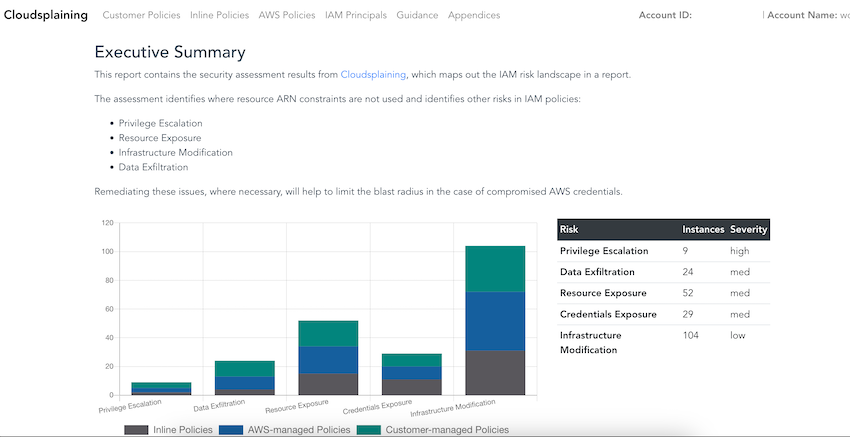
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report.
The assessment identifies where resource ARN constraints are not used and identifies other risks in IAM policies:
- Privilege Escalation
- Resource Exposure
- Infrastructure Modification
- Data Exfiltration
CloudMapper helps you analyze your Amazon Web Services (AWS) environments (using Python)
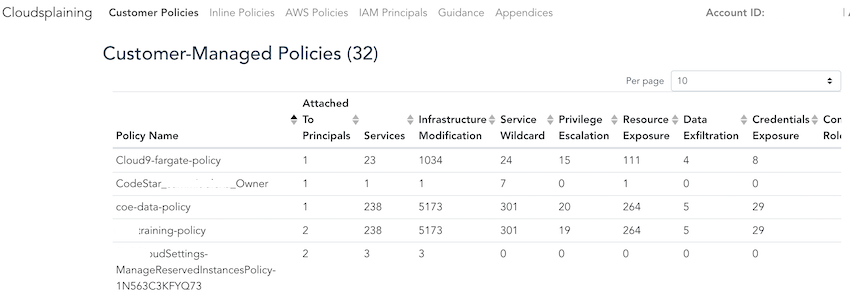
Why use it: The tool provides you a report with some risk in IAM policies (customer/inline/AWS) and the IAM principals (IAM Users, Groups, and Roles).
Is it popular?: On GitHub: Watch 29; Fork 143; Stars 1.6K
Recently updated? Yes. Last commit 3 days ago (347 commits in total)
URL: https://github.com/salesforce/cloudsplaining
3.6. Summary: Which tool should I use to perform security assessments on my account?
This is my personal opinion. If you have a different one, let me know in the comments at the end of this article!
- General security assessment:
prowlerorsteampipe - Security assessment based on CIS 1.5:
steampipe, prowler or cloudsploit - Richer tool security assessment based on frameworks:
steampipe - IAM specific security assessment:
cloudsplaining
4. Next steps
The next article related with open-source tools will be:
- How to help you with your code: to generate it (IaC), validate it (policy as code and compliance) and analyze it (static analysis/credentials) -> here